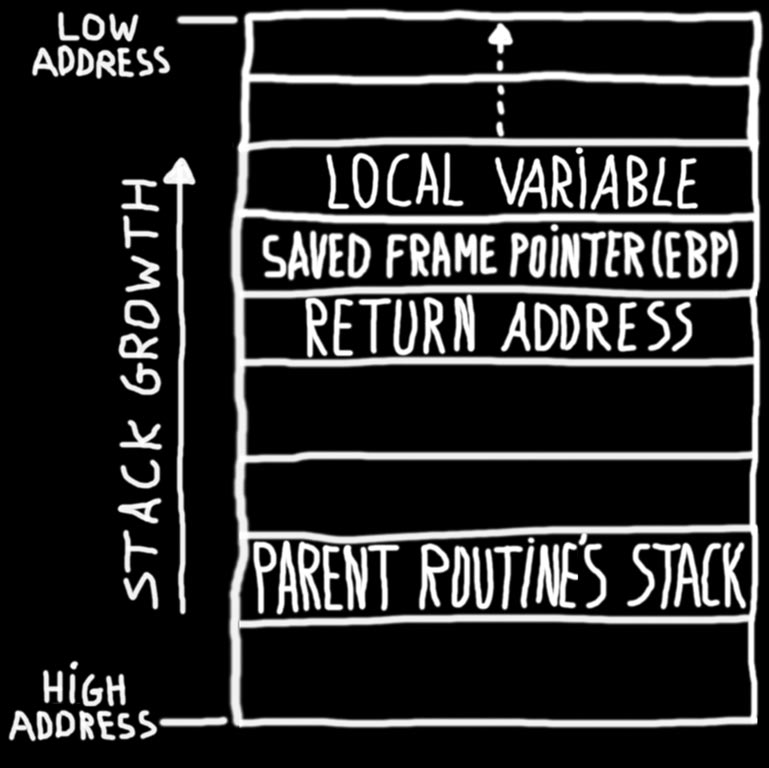
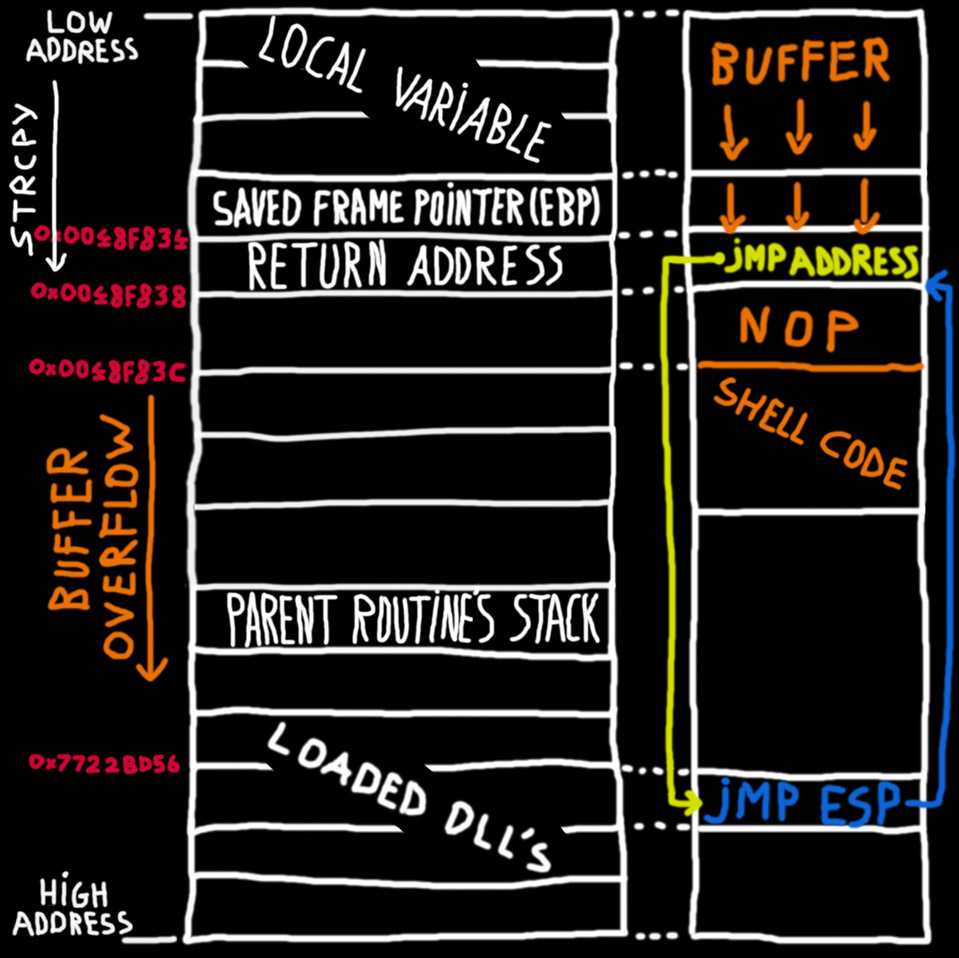
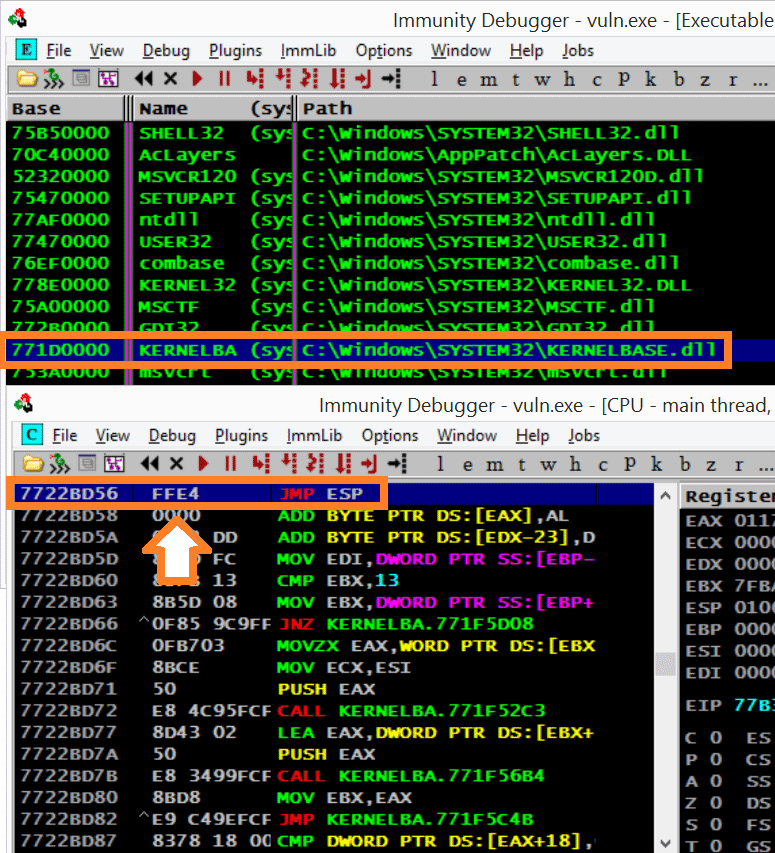
Buffer Overflow Lab.docx - Buffer Overflow Lab Based heavily on a lab developed by Wenliang Du of Syracuse University as part of the SEED labs series | Course Hero

Section 3.4: Buffer Overflow Attack: Attack Techniques 1 PowerPoint Presentation, Free Online Download PPT VZFVHQ